Managed Security Services
Fidelis Networks
Cyber Security Services
Assessments
To stay on top of potential vulnerabilities, you need an efficient and reliable process for assessing your security posture. This includes regular analysis, auditing as well as continuous monitoring of all systems and endpoints. By collecting detailed information on every asset connected to the network, we can help you build a comprehensive picture of all assets and risks.
Protection
In the past, businesses would take a passive approach to cybersecurity protection with firewalls and anti-virus software. Today, however, companies must be far more proactive in hunting threats and managing incidents. To get the most comprehensive visibility and protection possible for your organization, you’ll need access to a SOC team as well as EDR tools.
Compliance
Some sectors require compliance with certain frameworks and standards. This involves data privacy rules (e.g. GDPR) as well as industry-specific standards (e.g. PCI DSS). Some certifications beneficial regardless of your industry. By adopting the Cyber Essentials recommendations, businesses can protect themselves from 80% of known cyber-security threats.
Our foundation package is designed to harden your defenses
The ‘Assess & Prevent’ package is a comprehensive security solution that helps businesses protect themselves from data breaches and other cybersecurity threats. This provides businesses with a 360-degree overview of all aspects in which their networks are vulnerable, allowing them to take action to protect themselves.
Foundation Package
All the building blocks required to build a Strong Defense
Pricing starts at $250 per month
Vulnerability Scanning
How continuous vulnerability scanning works
Vulnerabilities refer to software coding flaws and system misconfigurations that can provide attackers with direct, unauthorized access to a system or network. For example, a hacker can exploit a software vulnerability to gain access to sensitive information or a malicious user can exploit a misconfigured service to gain privileged access.
Vulnerability scanners help prevent data breaches and system exploitation by ensuring systems are properly configured, patched and kept up-to-date.
Phishing Simulations
How phishing simulations help train users
Phishing is a rampant threat that can be enormously destructive. In most cases, hackers disguise themselves as trustworthy entities and ask users for their passwords and usernames in a convincing way. By obtaining this information, they are able to bypass security protocols simply by logging into the system.
Phishing simulations can be seen as a vaccine for phishing; just as to develop immunity to a virus, you need to administer a small dose of the virus. To defend against phishing in your company you similarly administer realistic simulations so that employees know how to identify and deal with real phishing threats when they arise.
Network Assessments
How do network audits and assessments work?
Network assessments play a critical role in cyber security, allowing businesses to find holes in their IT infrastructure that could be taken advantage of by hackers. Therefore, proactive network auditing and health checks should be part of every organisation’s regular maintenance routine.
It is impossible for any IT professional, no matter how competent, to predict every potential problem. A network assessment should thus be seen as vital for identifying and shoring up weaknesses in your system and ensuring that your cyber security posture is up to standard.
Dark Web Monitoring
How dark web monitoring works
The dark web is a set of anonymously hosted websites that can be accessed with specific software, most commonly “TOR” (The Onion Router). These dark websites contain online marketplaces for exchanging illegal goods, including personal information stolen from real people.
It’s like a hacker’s paradise in real life, where you can purchase information that should not be accessible to anyone else. For this reason, it is necessary to monitor the dark web for data breaches. With Fidelis Networks’s specialized tools, organizations can detect any potentially sensitive data that has been exposed and take the necessary steps to protect it.
User Awareness Training
How user awareness security training works
Our courses are delivered in an interactive and easy-to-absorb way, either through bite-sized browser modules or instructor-led sessions. Furthermore, we reinforce what users learn with tests such as mock phishing simulations and other attack scenarios. This way, employees can remain informed about the ever-evolving threat landscape and take active steps to protect themselves and your business.
User awareness training is one of the most effective cyber security tools available to businesses, as hardened users are more likely to spot and report suspicious activity than those who have never encountered a cyber attack in real life.
Our Compliance packages
The objective is to establish a framework of standards for how a modern business should manage their information security by addressing people, processes, and technology. We make sure you are compliant.
Compliance Packages
Frameworks for legal and best practice security compliance.
Cyber Essentials
How Cyber Essentials certification works
There are two types of certification available: Cyber Essentials and Cyber Essentials Plus. Both require the same security protections, but the Plus version requires technical verification to be performed in person. If you want to bid on government contracts, then you are required to have at least the Cyber Essentials certification.
Why should you become Cyber Essentials certified? Well, it is a great way to demonstrate to your customers and potential customers that you take cybersecurity seriously, and that you have taken the steps necessary to protect yourself from cyber-attacks. It is also a cost-effective way of doing so; most companies will find that they can get the certification in a matter of days or weeks, rather than months or years.
ISO 27001 Certification
How becoming ISO 27001 certified works
The objective of ISO 27001 is to establish a framework of standards for how a modern business should manage their information security by addressing people, processes, and technology. ISO 27001 is a part of the ISO 27000 series of information security standards.
This framework helps organisations establish, implement, operate, monitor, review, and continually improve an Information Security Management System (ISMS). ISO 27001 ensures that organisations can deliver the same consistent level of security to all customers and partners, no matter where they are in the world and regardless of their size or industry.
ISO 22301 Certification
How becoming ISO 22301 certified works
Investing in ISO 22301 could be loosely described as an insurance policy for your company. By implementing business continuity practices compliant with this international standard, you are developing a system that will save your company money in the long run by either preventing disruptive incidents from occurring or by becoming capable of faster recovery.
The upfront cost of investing in ISO 22301 is far smaller than the long-term cost of disruption, downtime, or data loss. Going through ISO 22301 helps businesses to fully understand how their data is stored and backed up, and how the entire business can be recovered in the event it is ever necessary. It also helps to identify areas of weakness and inefficiency that could cause disruptions in the first place.
GDPR Compliant
How becoming GDPR compliant works
Compliance with GDPR isn’t just a box-ticking exercise; it should be something that is prioritised whenever implementing or reviewing any technical or organisational controls. Organizations need to be accountable for how they handle data, which means demonstrating compliance is essential.
On paper, GDPR compliance looks like a complicated process; however, Paladin makes it easy to manage with our unique online management system, making it simple for business owners and authorised staff members to manage changes to policy when required.
PCI DSS Compliant
How becoming PCI DSS compliant works
The Payment Card Industry Security Standards Council (PCI SSC) provides specification frameworks, tools, measurements, and support resources to help ensure payment card data security. The Payment Card Industry Data Security Standard (PCI DSS) is the foundation of the council since it encompasses prevention, detection, and reaction strategies for handling potential security incidents.
Everyone from merchants processing card payments to service providers developing applications used for processing card transactions must abide by the PCI DSS rules and standards. If your organization accepts credit or debit cards, it is worth reviewing whether PCI DSS is a requirement for your business.
User awareness training is one of the most effective cyber security tools available to businesses, as hardened users are more likely to spot and report suspicious activity than those who have never encountered a cyber attack in real life.
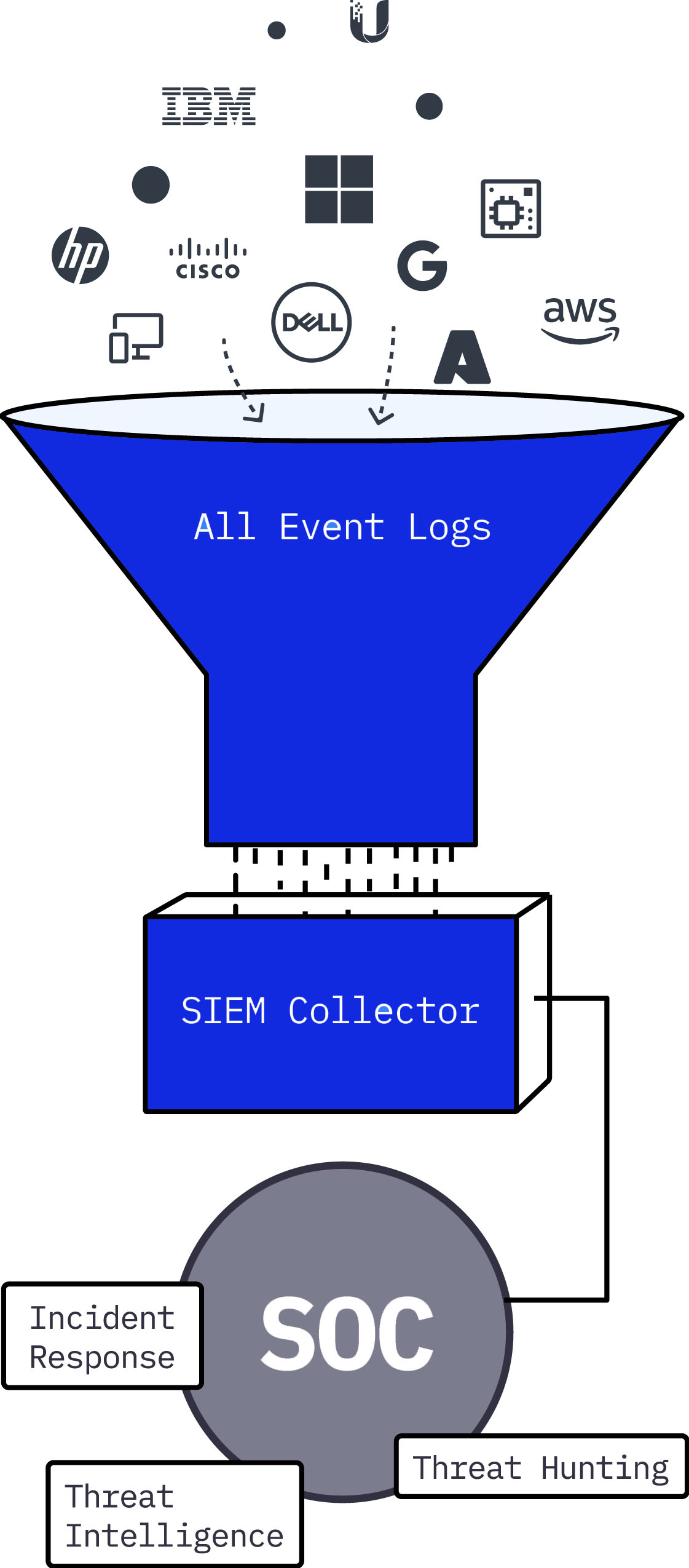
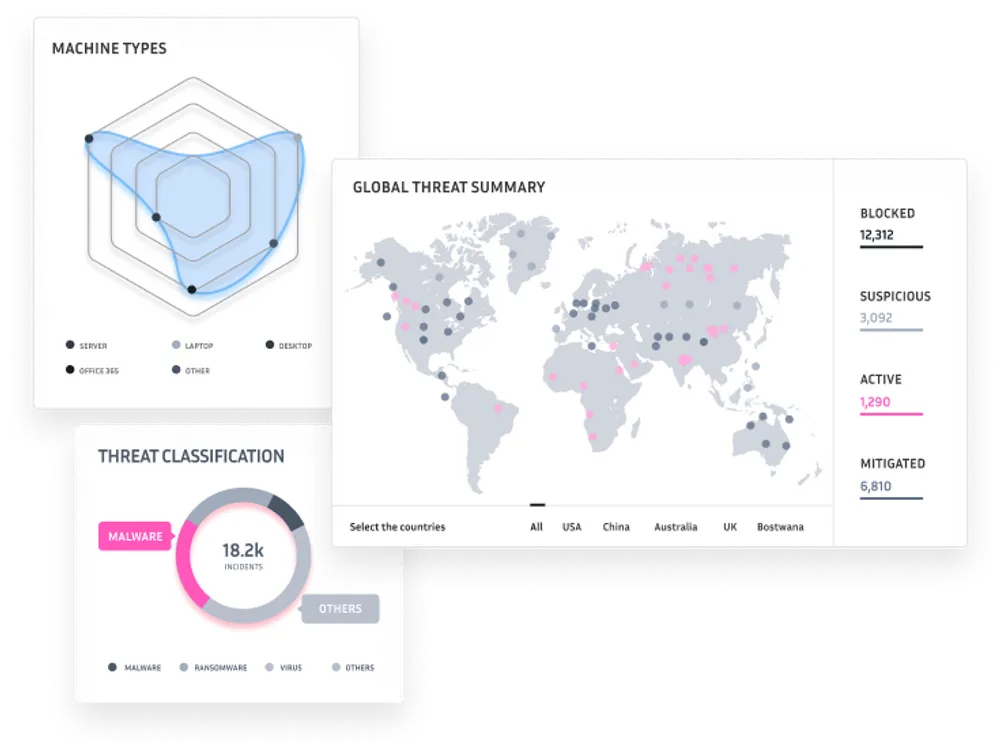
SECURITY OPERATIONS CENTER
Monitor your business in real-time with our Security Operations Center
Most businesses wanting to maximise their cyber security capabilities hire in-house security experts full-time. These individuals continuously monitor networks and hunt down threats; however, this option usually comes with a high price tag. The alternative is using an outsourced SOC, or Security Operations Center, at a fraction of the cost.
A SOC is vital for understanding if your security has been breached, and can also help determine how the breach occurred. Without a SOC, it would be difficult to impossible to tell if you were under attack or had already been infiltrated.
The security operations centre (SOC) collects data from across an organization’s IT infrastructure and decides how to respond. Workstations, servers, and other devices all send telemetry to the SOC, which must then make sense of it all and decide whether or not the event should be investigated. In the event of an incident, the SOC provides a rapid and effective response to help minimize the impact of any attack.
With so many advanced threats these days, it’s more important than ever for organizations to have a central command post that can collect context from diverse sources, and act immediately.
Fidelis Networks SOC team is responsible for detecting, responding to, and remediating critical cybersecurity incidents. Our arsenal of tools includes automated and manual methods, providing a redundant layer of action to effectively detect, investigate, contain, report on, and recover.
We will help turn your business into a highly secure fortress by locking down the environment with 360-degree visibility across your infrastructure. Our team of experienced cyber professionals is here to help protect your systems and data with cutting-edge solutions and rapid response times.
SOC Packaged Service
SOC is part of our advanced add-ons
At Fidelis Networks, we pride ourselves on delivering the best cyber defence available. We know that cybersecurity is a complex process that requires many different components working together to be effective. Our SOC service is just one part of this puzzle. To make things easier for you, we have created packages that come with several of our services so you can get the full protection you deserve.
Achieve total control of your cyber security with our comprehensive range of services. Our team of expert engineers will review your existing IT infrastructure and practices, and evaluate the risk posed by potential cyber threats.
We provide the implementation of industry-leading technologies and frameworks to enhance your current setup, as well as customised development of security protocols customised to fit your operations.
We provide cyber security and monitoring services that you can rely on. We give you access to sophisticated features from our Security Operations Center (SOC), that handles security incidents in real-time, 24/7.
Call Us: If you are experiencing an urgent issue or are under attack, please don't hesitate to call us at 512 651 8300
Email Us: If your query requires more detail than what our contact form can include, feel free to email us instead.
Our headquarters are open from 8:30 am to 6 pm, Monday through Friday. Our ops team operate 24/7.
It is worth assessing your position
When it comes to cyber security, one of the most important things you can do is to assess your risk regularly. Understanding where your vulnerabilities lie allows you to place the necessary protections to keep your business safe, which is something our experts can help with. We know that cybersecurity can be daunting, but Fidelis is here to make it simple. Contact us today for a free consultation!

Take the first step towards fortifying your business against cyberattacks
Are you interested in gauging how prepared your business is to combat cyber-attacks? At least understanding the specifics of each vulnerability and loophole will provide you with an opportunity to safeguard those areas before anything bad happens. No matter what your cyber security objectives are, we’re here to help.
It was found that in 93% of cases, an external attacker can breach an organization’s network perimeter and gain access to local network resources.
Global average cost is a Data Breach is $3.92 million. Cost includes loss of business, data forensics, investigative costs, and post-breach mitigation costs.
83% of consumers stop spending with a business temporarily after a security breach, and 21% say they will never return to a business post-breach.